Story
Policy Compiler for Secure Agentic Systems
Key takeaway
Researchers developed a policy compiler to embed complex authorization rules into prompts for AI assistants, making them more secure for real-world deployment in sensitive contexts like customer service and data access.
Quick Explainer
The Policy Compiler for Agentic Systems (PCAS) introduces a novel approach to enforcing security and compliance policies across complex multi-agent environments. Instead of embedding policies directly in agent prompts or relying on imperfect machine learning detectors, PCAS models the system as a dependency graph and compiles declarative authorization rules into a reference monitor. This runtime enforcement mechanism provides verifiable policy specification, deterministic decision-making, and detailed transparency - ensuring that agent actions adhere to the specified constraints without compromising functionality. By decoupling policy from prompts and leveraging formal reasoning over the system's causal structure, PCAS addresses key limitations of existing policy enforcement techniques for LLM-powered applications.
Deep Dive
Technical Deep Dive: Policy Compiler for Secure Agentic Systems
Overview
The work presented in this technical deep-dive briefing introduces the Policy Compiler for Agentic Systems (PCAS), a system that enables deterministic enforcement of declarative authorization policies across multi-agent systems.
Problem & Context
Large language model (LLM)-based agents are increasingly deployed in complex organizational contexts, such as customer service, pharmacovigilance, and software engineering, where their actions must adhere to specific security and compliance constraints. However, existing approaches that embed policies directly in agent prompts or use LLM-based detectors suffer from fundamental limitations:
- Prompt-embedded policies are ambiguous, difficult to analyze, and provide no enforcement guarantees.
- LLM-based detectors are vulnerable to adaptive attacks that can evade the detector while still manipulating the agent.
Methodology
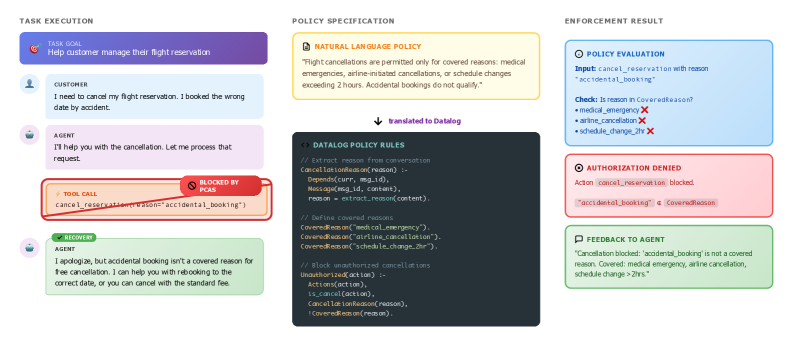
To address these limitations, the authors of PCAS take a fundamentally different approach. They model the agentic system as a dependency graph that captures causal relationships between agent actions, messages, and tool results. They then express authorization policies as declarative rules in a Datalog-derived language, which are compiled into a reference monitor that mediates all agent actions before execution.
Key aspects of the PCAS methodology include:
- Maintaining a fine-grained dependency graph to support causal reasoning about policy violations
- Using a Datalog-based policy language that enables recursive queries over the dependency graph
- Automatically instrumenting existing agentic systems to enforce policies deterministically at runtime
Data & Experimental Setup
The authors evaluate PCAS across three case studies:
- Information flow policies for prompt injection defense: Agents with access to sensitive data and email capabilities are tested against adversarial prompt injection attacks.
- Customer service policies from the `τ²-bench` benchmark: Agents navigate complex business rules around booking, cancellation, and refund workflows.
- Pharmacovigilance system with FDA data access control: Agents in a multi-step workflow must obtain supervisor approval before querying sensitive drug safety databases.
In each case, the authors compare the performance of non-instrumented agents (where policies are embedded in prompts) against PCAS-instrumented agents that rely solely on runtime enforcement.
Results
The key findings from the PCAS evaluation include:
- Functionality: Runtime enforcement preserves task success for policy-compliant workflows, with minimal performance impact on legitimate actions.
- Compliance: PCAS-instrumented agents achieve significantly higher policy compliance rates compared to non-instrumented baselines, eliminating violations like adversarial reframing, over-helpful service additions, and unauthorized API access.
- Overhead: The additional latency introduced by PCAS is modest, averaging 20% longer execution times, with minimal impact on token costs.
Interpretation
The PCAS approach provides several important benefits over prompt-based or LLM-based enforcement:
- Formal policy specification: Datalog rules constitute a verifiable, analyzable artifact, enabling policy authors to systematically test for completeness and correctness.
- Deterministic enforcement: The reference monitor's authorization decisions depend solely on the policy specification and observed execution trace, not on the agent's reasoning.
- Transparency and auditability: PCAS generates detailed traces explaining why actions were allowed or denied, supporting compliance and incident investigation.
Limitations & Uncertainties
- PCAS assumes all relevant information flow is captured through the instrumented message-passing infrastructure. Agents with arbitrary code execution may communicate through side channels that bypass instrumentation.
- Translating natural language policies into formal Datalog rules requires careful analysis, though recent advances in natural language to formal specification translation suggest promising directions for reducing this effort.
What Comes Next
Potential future work includes:
- Automated dependency inference to reduce manual instrumentation effort
- Improved feedback generation by deriving relevant rules from authorization query failures
- Extensions to the policy language for expressing temporal constraints like rate limits
- Formal verification of the policy compiler's correctness guarantees
Overall, the PCAS approach demonstrates the value of formal policy enforcement in agentic systems, providing a foundation for deploying LLM-powered agents with explicit, auditable, and deterministic authorization guarantees.